Learn About John The Ripper: Password Cracking & Security
Is your digital fortress truly secure? In today's interconnected world, where data breaches are commonplace, understanding password security is no longer optional it's essential, and John the Ripper emerges as a vital tool in this ongoing struggle.
The landscape of cybersecurity is a constantly evolving battleground, with attackers continuously honing their skills and techniques. Weak passwords remain a primary vulnerability, offering a readily accessible entry point for malicious actors. The human element, with its tendencies toward predictability and ease of use, often becomes the weakest link in the security chain. We will delve into a powerful, yet often misunderstood, tool: John the Ripper, a password cracking utility designed to identify and expose these vulnerabilities. This article provides a comprehensive overview of John the Ripper, its capabilities, and its practical applications. We'll explore its core functionality, the accompanying graphical interface, Johnny, and the importance of responsible password auditing.
John the Ripper is more than just a tool; it's a philosophy of proactive security. It embodies the principle that vigilance and constant assessment are necessary to maintain a robust defense against cyber threats. It encourages systems administrators to act as their own adversaries, probing their systems for weaknesses and fortifying them before malicious actors exploit them. The tool's ability to test passwords and identify potential vulnerabilities allows administrators to establish and enforce strong password policies, thereby raising the overall security of the network. The utility's very design emphasizes the need for strong, randomly generated passwords and regular password audits. Understanding its capabilities and limitations empowers security professionals to adopt a risk-based approach, prioritizing security efforts and resources where they are most needed.
Before we proceed, it is important to understand that utilizing tools like John the Ripper can have ethical and legal implications. It is crucial to employ such tools responsibly and only with explicit authorization. Unauthorized password cracking activities are illegal and can result in severe penalties. The information presented here is intended for educational purposes, to promote responsible cybersecurity practices, and to aid in securing your own systems.
John the Ripper, at its heart, is designed to help systems administrators identify weak passwords. It works by attempting to "crack" passwords using various methods, including dictionary attacks, brute-force attacks, and hybrid approaches. A dictionary attack involves comparing the password hashes against a database of commonly used words and phrases. A brute-force attack systematically tries every possible combination of characters until the correct password is found. The tool's strength lies in its ability to efficiently test a large number of password candidates, exposing those that are easily guessable or susceptible to cracking.
The core of John the Ripper's functionality is its ability to understand different password hash formats. Passwords, when stored, are not saved in plain text; instead, they are converted into a "hash" using a cryptographic algorithm. John the Ripper supports a wide array of hash types, including those used by Unix systems (such as MD5, SHA-1, and bcrypt), Windows systems (NTLM), and various other applications and services. This versatility makes it a powerful tool for testing the security of a wide range of systems. The tool is cross-platform compatible, allowing it to be used on Windows, macOS, Linux, and other operating systems.
One of the most significant benefits of John the Ripper is its portability. The tool's ability to operate on different platforms is a key advantage, as it provides administrators with a consistent security assessment capability regardless of the underlying operating system. Installation typically involves unpacking the downloaded archive, making it accessible to users. This simplicity ensures that even users without extensive technical skills can implement password audits.
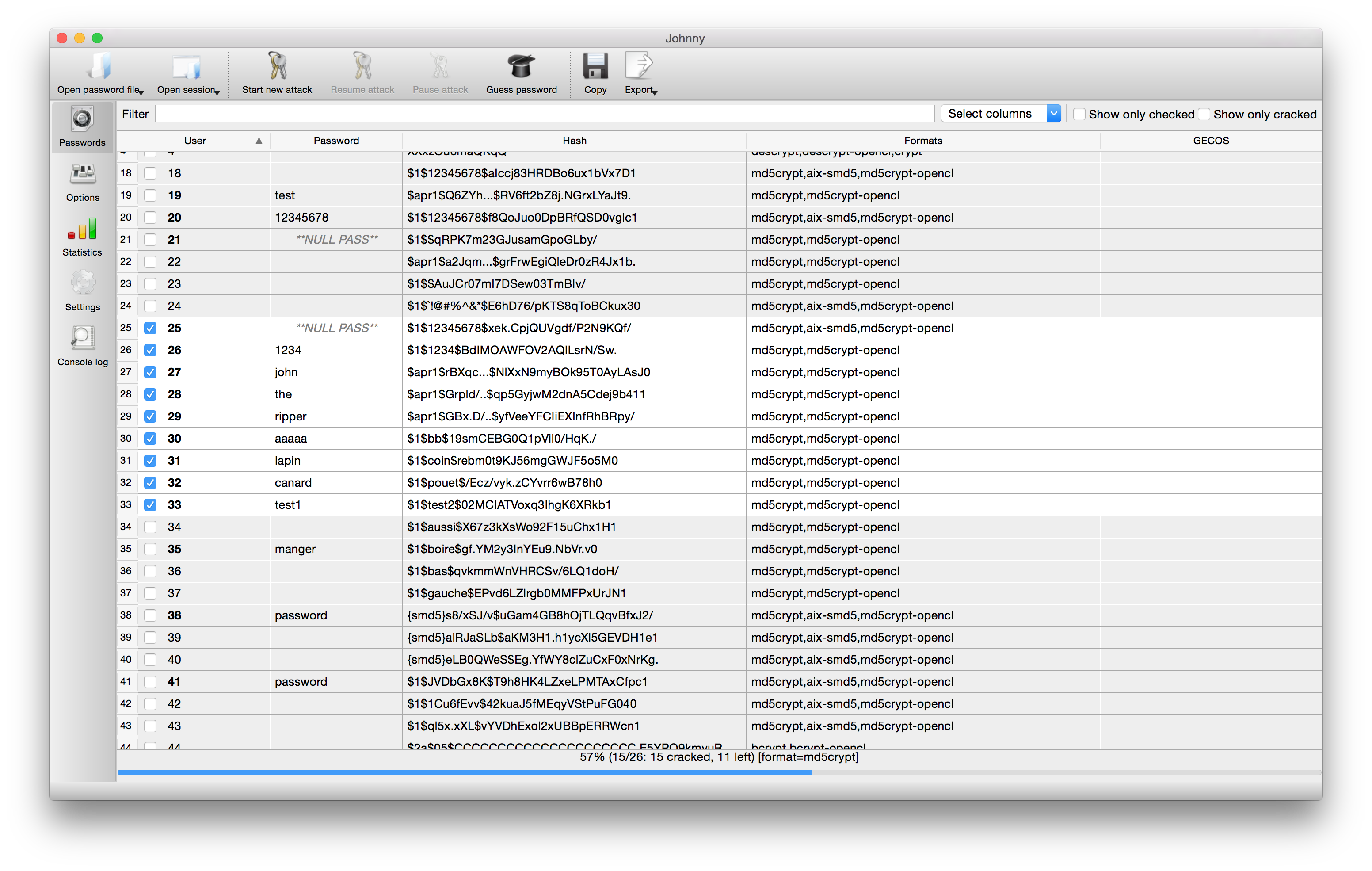
John the Ripper isn't just a command-line tool. It offers a graphical interface, Johnny, which simplifies the cracking process. Johnny provides a user-friendly front-end, allowing even less experienced users to effectively utilize John the Ripper's capabilities. It simplifies the selection of attack modes, the management of wordlists, and the analysis of results. Johnny's intuitive design makes it easier to initiate password cracking attempts, monitor progress, and interpret findings. It also helps users to access the more advanced functionalities of John the Ripper without having to learn the command-line syntax. It serves as a crucial asset in enhancing the usability of the tool, encouraging a broader spectrum of security professionals to conduct password audits.
The evolution of John the Ripper demonstrates a commitment to adapting to new password hashing algorithms. This ensures that the tool maintains its relevance in the face of emerging security threats and vulnerabilities. As new password hashing algorithms are developed and implemented, John the Ripper is constantly updated. This commitment to ongoing development enhances its effectiveness. These updates keep the tool relevant in the face of evolving security challenges.
For those seeking a user-friendly experience, there's Johnny, a graphical interface that seamlessly interacts with the core functionality of John the Ripper. Johnny simplifies the process, making the powerful password cracker accessible even to those less familiar with command-line interfaces. Its intuitive design makes it easy to initiate password cracking attempts, monitor progress, and analyze results, thereby democratizing the power of John the Ripper.
When considering the use of John the Ripper, it is important to understand the ethical and legal boundaries. Password cracking without authorization is illegal and harmful. This tool is meant to be used in the defense of systems, and never for malicious activities. Always ensure you have explicit permission before testing the security of any system.
The tool's open-source nature fosters community contributions, ensuring its continued evolution and effectiveness. The collaborative spirit of the open-source community drives innovation and promotes the rapid identification and mitigation of security vulnerabilities. With open-source software, the source code is available to the public, allowing anyone to inspect, modify, and distribute it. This transparency helps identify vulnerabilities, improve security, and foster innovation.
The use of John the Ripper, however, is just a single facet in a robust security strategy. John the Ripper is not a silver bullet. It provides a detailed analysis of password strength, and identifies system vulnerabilities. The analysis helps admins prioritize security efforts, and strengthen their defenses. While John the Ripper can identify weak passwords, it's only part of a larger comprehensive security approach.
The integration of John the Ripper with other security tools, like intrusion detection systems (IDS) and security information and event management (SIEM) platforms, allows for a holistic approach. Integrating with SIEM platforms, provides real-time alerts on password cracking attempts, enabling security teams to quickly respond to suspicious activities. The effectiveness of John the Ripper depends on the user's ability to understand its findings, analyze the underlying vulnerabilities, and take appropriate action.
Password security is a dynamic field; the principles of password management are regularly updated. The recommendation includes a diverse range of best practices, from enforcing strong password policies to promoting the use of multi-factor authentication. Regularly auditing passwords, using John the Ripper, makes sure systems remain secure. Regularly updating John the Ripper guarantees that it can withstand current password security measures.
The ongoing journey towards stronger password security is a shared responsibility. The goal is to protect sensitive data from attackers. When used correctly and ethically, John the Ripper is a powerful asset. It provides a strong defense against digital threats. By understanding its capabilities, adhering to legal and ethical boundaries, and integrating it into a comprehensive security strategy, organizations can significantly improve their overall security posture and reduce their risk of a data breach.
The journey towards establishing strong passwords should be ongoing. John the Ripper, along with other tools, helps in the continuous effort. Understanding its strengths and weaknesses, and utilizing it responsibly, is critical. Proactive measures are necessary to protect digital assets. John the Ripper is an important tool in that effort. The path to robust digital security is a journey, not a destination. It requires constant vigilance, adaptation, and a commitment to evolving best practices.
The use of password cracking tools like John the Ripper raises an important discussion. It highlights the ongoing tension between cybersecurity and the need to balance security. The benefits are significant, but it necessitates that the tool be used with ethical and legal care. By understanding its capabilities, and following ethical guidelines, security professionals can greatly improve the safety of their digital environment.
In conclusion, John the Ripper remains an indispensable tool for anyone serious about password security. Its ability to identify weaknesses and promote proactive security measures is unmatched. Embracing the responsible use of John the Ripper represents a significant step towards a more secure digital world.